INF047
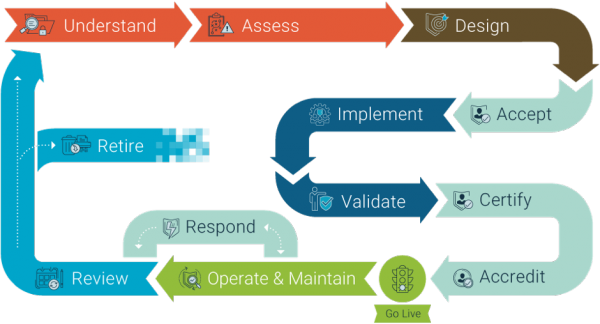
The information security lifecycle describes the process to follow to mitigate risks to your information assets:
INF047
The information security lifecycle describes the process to follow to mitigate risks to your information assets:

INF023
To implement the right security measures, you need to understand what information you have and how valuable it is (INFOSEC1)
A comprehensive inventory will help you to find out what types of information and ICT systems your organisation has, including those that support business continuity and disaster recovery plans.
Your organisation might have many different types of information and information assets, such as:
For each type of information or ICT system, you should record:
You must understand the value, importance, and sensitivity of your information. This will determine the minimum requirements you need to protect it from harm.
Not all information should be treated equally. Some information is more valuable or sensitive, requiring a greater level of protection. The Business Impact Levels (BILs) is a tool that can be used to assess the value of your information and what impact might occur if your information is compromised.
Along with assessments of event likelihood, threats, and vulnerabilities, BILs should inform a robust risk assessment.
INF024
Based on the value of your information and equipment, classify and assign protective markings to inform your people on how to handle the information and protect it from harm.
All New Zealand Government agencies must follow the New Zealand Government Security Classification System. It informs agencies about their responsibilities for assessing, classifying, managing, and controlling official information.
The system is intended for use by all New Zealand government employees, contractors, and anyone else with access to official information. The system helps you to:
A security classification specifies how people must protect the information and equipment they handle.
Security classifications can be divided into two types of information:
The classifications for material that should be protected because of public interest or personal privacy are:
The classifications for material that should be protected because of national security are:
At times, there may be a relationship between security classifications for official information and BILs. The security classifications directly match the BILs when considering the confidentiality of individual documents or files. However, this does not necessarily apply to collections of assets.
However, a protective marking, or confidentiality, of an asset isn’t the only factor to consider when you work out a BIL. You need to consider all factors affecting the security of an asset before you apply a BIL. BILs also need to consider integrity and availability.
The table below shows the likely relationship between protective markings and BILs:
Likely relationship between protective markings and BILs for individual files or documents
| Protective marking level | Business impact levels |
| UNCLASSIFIED (may not be marked) | 1 Low |
| IN-CONFIDENCE | 2 Medium |
| SENSITIVE or RESTRICTED | 3 High |
| CONFIDENTIAL | 4 Very high |
| SECRET | 5 Extreme |
| TOP SECRET | 6 Catastrophic |
Consider extra security measures for collections of information (aggregated information). Aggregated information can be more valuable than the single pieces of information it’s made up of, so your organisation might need extra security measures to protect it. Ask yourself ‘What could be deduced if the collection were breached?’
Aggregated information includes collections of physical documents and collections of information stored in your ICT systems.
The Business Impact Levels (BILs) is a tool that can be used to assess the value of your aggregated information and what impact might occur if the confidentiality, integrity or availability of your aggregated information is compromised.
Classify and label New Zealand Government equipment in line with Product Classifying and Labelling(external link).
Archives, information management, and public records
Privacy and data protection
Protective Security Requirements
INF048
To protect your organisation's information, you have to understand its value, and how it could be threatened.
INF025
You need to think about the vulnerabilities and threats you face and their impact on your organisation. Consider the following questions to help you assess your organisation’s risks:
Identify areas where your organisation might be vulnerable to security breaches (deliberate or accidental). Determine which vulnerabilities might be exploited and how this might be limited.
A vulnerability is a weakness in your information security defences. To assess your vulnerabilities, you need to understand where your defences are weak. An annual security self-assessment is a great starting point for identifying your security vulnerabilities.
The following resources have more information on essential information security practices that organisations should adopt.
Identify and document the potential threats to your information security and ensure that this information is kept current. Ask yourself, ‘Who would benefit from having access to our organisation’s information and what information would they want?’
Threats to the security of your information can come from inside and outside your organisation. Your information in all forms — electronic, printed and spoken — needs appropriate protection. Information stored and processed on IT systems or mobile devices is vulnerable to cyber-specific threats.
Threats evolve continually. Your chief security officer (CSO) should refer to the following threat catalogues to stay ahead of the emerging threats:
Assess how your organisation would be impacted if your information security is breached. Think about the confidentiality, integrity, and availability of your information. Think about how your people, clients, and partners would be impacted.
Consider the impact on your organisation if:
INF026
Once you understand the value of your information and the vulnerabilities and threats you face, assess the risks and identify the appropriate security measures you will adopt. Your risk assessment will inform your decisions about design, certification and accreditation.
During your risk assessment, consult with all relevant people who have insight into the business and security risks that you might face, such as your chief security officer (CSO), chief information security officer (CISO), information security practitioners, and risk owners. The CSO should keep abreast of the organisation’s protective security policy and the threat environment, for robust risk planning and management.
Organisations should apply sound security risk management practices that follow ISO 31000:2018 and the HB 167/2006 Security risk management.
The Government Chief Digital Officer (GCDO) provides useful guidance on information security and privacy risk management techniques and tools.
Supporting Documents and Information
Once you have defined your risks, prioritise and plan your risk mitigation strategies.
Give high priority to vulnerabilities that may result in the release of private or sensitive information. You can use a simple equation:
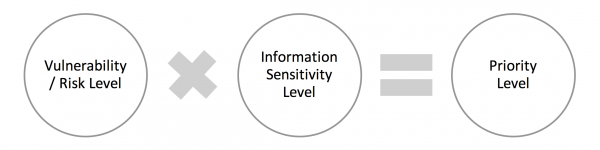
Figure: Vulnerability/Risk prioritisation equation
For example, a high risk vulnerability (such as cross-site scripting or weak password strength) in a standalone system with unclassified information (considered ‘low’ sensitivity) may have a low priority. The same vulnerability in an application that’s linked with others, and that holds citizens’ confidential, financial, or private details may have a ‘high’ priority.
INF027
Assessing your current security is the first step in planning an information security management programme.
You should ask yourself the following questions about your existing security measures.
The New Zealand Information Security Manual(external link) (NZISM) identifies the information security controls organisations should have in place.
INF049
Based on the risks your organisation faces, you will need to design the appropriate information security measures your organisation needs to protect your information’s confidentiality, integrity and availability.
As you plan changes to your information landscape, you will need to reconsider your existing security measures and extend them appropriately (INFOSEC2). The New Zealand Information Security Manual(external link) (NZISM) specifies mandatory baseline controls for New Zealand Government agencies, based on the classification of your information, and a series of additional controls to treat your identified risks.
INF028
Effective security for an information asset can be achieved by using several different layers of security measures.
This approach is referred to as 'defence in depth' — the security of an asset is not significantly reduced with the loss or breach of any single layer of security.
A ‘defence-in-depth’ strategy:
A simple example is preventing malware from infecting IT systems. You might apply three or more layers of defence:
If any one system fails to detect a piece of malware, another system will detect it and prevent the malware from running. It’s important to use a diverse and complementary range of capabilities so each layer can catch and prevent an intrusion that another layer may have missed.
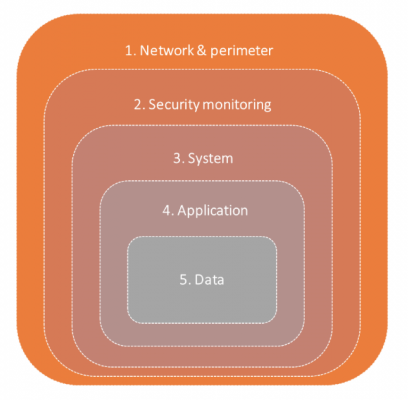
Figure: An example of layers of control in a ‘defence in depth’ information security system in an enterprise environment
INF029
When you design your security measures, address your critical information security risks and vulnerabilities including your cyber-security threats, information security culture, security products, and processes.
Your organisation must have measures in place for controlling access to all information, ICT systems, networks (including remote access), infrastructure and applications, as defined in the NZISM: Access Controls.
Areas to consider include:
The New Zealand Information Security Manual(external link) (NZISM) is a resource that New Zealand Government agencies must use (and private organisations can use) to ensure your organisation complies with its obligations. It is important to carefully assess which controls apply to your organisation.
The design of all your security measures for information, ICT systems, networks (including remote access), infrastructure, and applications must be lawful.
Resources for designing information security
You should ensure that all defence layers have adequate security measures. Use the resources below to support the design of your security measures:
Network and perimeter security
Security monitoring
System security
Application security
Data security
Also refer to Information management guidance and resources(external link) — digital.govt.nz — including Common capabilities panel, Government Enterprise Architecture NZ (GEA-NZ) standards, web standards, web services standards, cloud services, and open government.
Legislation on information and privacy
You should also be familiar with the legislation on information and privacy.
Meeting the minimum standards is often not enough, but the cost of ultimate security can be prohibitive. Your information security framework should be pragmatic while still ensuring that your critical risks are adequately addressed.
For more information email: info@ncsc.govt.nz
The security requirements you identified during the design phase should also be in your business continuity and disaster recovery plans.
Business continuity management defines the actions to take to continue operating during a significant service interruption, attack or other incident, and then to return to normal operation after the incident.
You will need to develop and regularly test your plans to prepare your organisation for smooth operation during an incident, and ensure that you can resume normal operations as soon as possible after the incident. Your organisation’s resilience depends directly on its ability to confront the hazards and continue to achieve its defined outcomes.
Given the increasing dependence on information systems to deliver your products and services, you need to consider the resilience of the ICT systems that hold and process your critical information. Key metrics for your ICT disaster recovery plans should include:
For more information go to Business continuity management.
All New Zealand Government agencies must design their security measures in line with the New Zealand Government Security Classification System. Refer to: How to protect information for specific required security measures.
This guidance provides a consistent and structured approach to protectively marking and handling official information and material subject to the New Zealand Government Security Classification System.
This guidance provides the procedures for protectively-marked information and material including:
Incorporate the appropriate security measures for the specific scenarios that you assessed during your risk assessment.
INF030
During this phase of the information security lifecycle, you implement the agreed security and privacy measures including policies, processes, and technical security measures.
Work with your suppliers to ensure that they understand and can meet your security requirements. Build your security requirements into your contractual arrangements.
Security weaknesses in suppliers can compromise otherwise robust security measures in other parts of your business. Remember to account for the information risks involved in the ICT system development lifecycle, such as development providers accessing and using test data or defect tracking systems.
Consider separating development, test and operational facilities to reduce the risk of unauthorised access or changes to systems.
Supporting documents and information
Only do system testing after all security measures have been implemented and before acceptance. Use an effective change control process to ensure that changes conform to relevant standards.
Use a formal management process to control changes to all information systems.
Supporting documents and information
INF031
Validate your organisation’s information security measures to find out if they’ve been correctly implemented and are fit for purpose (INFOSEC3).
Your chief information security officer (CISO) must determine whether security measures are acceptable for the risks your organisation faces.
The validation step provides senior executives with the confidence that information and its associated technology are well-managed, risks are properly identified and mitigated, and governance responsibilities can be met.
Conduct the appropriate certification and accreditation processes required for the type of security measures being implemented.
ICT systems must follow the certification and accreditation process defined in the New Zealand Information Security Manual (NZISM)(external link). They must also reflect the mandatory controls in the manual.
Physical security of buildings, facilities and equipment requires additional certification and accreditation. Complete this before you get your ICT system accredited. See the Management protocol for physical security for more information.
Supporting documents and information
INF050
Threats, vulnerabilities, and risks evolve over time as technology, business, and information demands change. Security measures must keep pace with this change to remain relevant and effective.
INF032
To manage vulnerabilities in your information security, take the following action.
Threats are continually evolving. Your chief security officer (CSO) should use the following threat catalogues to stay abreast of emerging threats:
INF033
Your security measures are only effective if they reflect your actual assessed risks and you keep them up to date as risks and threats emerge.
INF034
Good management is critical to reducing the impact of security incidents and recovering quickly. Incident response should be a key part of your overall security framework.
A security incident is:
You’ll need to provide your people with the guidance and resources to act in a timely, coordinated manner to prevent or respond to security incidents that could compromise critical and sensitive information. Develop and regularly test these processes and procedures as part of your business continuity and disaster recovery planning.
Supporting documents and information
When an incident happens, act quickly to reduce any impact and help your organisation recover as quickly as possible. Later you might also need to restore the confidence of any partners or clients affected by an incident.
Supporting documents and information
INF035
Undertake regular reviews to ensure your security measures remain fit for purpose.
Identify changes in how you use and organise your information, and any changes required by legislation. Use this information to inform improvements.
To minimise the risk of disruption to organisation business processes, you should carefully plan and agree suitable audit requirements for operational systems.
Minimise the opportunity for unauthorised access to information system audit tools to limit the potential to misuse or compromise them.
Regularly monitor, review, and audit your security measures so you know the degree to which your information security policies are being implemented and followed. This should include:
Supporting documents and information
Change is a given. You need to identify which changes in your environment might affect your information security and be prepared to restart your information security lifecycle.
Consider these questions to inform changes and improvements.
Your review will identify required changes to your information security requirements. These changes may trigger either the:
INF036
When your information and supporting ICT systems are no longer required, they need to be archived, destroyed, repurposed, or disposed of securely.
The New Zealand Information Security Manual (NZISM) offers advice and controls for managing information and systems that have reached the end of their lifecycle.
Consider these questions:
Make sure you take into account relevant legislation, the requirements in the New Zealand Information Security Manual, and best practice standards.
Supporting documents and information