Limiting access to those with a ‘need-to-know’
What is ‘need-to-know’?
In common practice, the phrase ‘need-to-know’ is often used as a shorthand explanation of why information cannot be shared, as in ‘sorry, that’s need to know’.
This is an incorrect interpretation. The concept of ‘need-to-know’ is simply that one should confirm that it is appropriate to share a piece of information before one does so.
For example, while a piece of intelligence may be shared relatively widely the details of the source of that information may be much more tightly guarded. Equally, a doctor at a hospital does not have a ‘need-to-know’ the details of a patient that they are not treating.
The words ‘need-to-know’ of themselves have no explanatory power. ‘Need-to-know’ simply means that there should be a good reason for an individual to have access to information.
Who decides on ‘need to know?’
Information is ‘originator controlled’ and the originator and controlling organisation or government decides if the information should have restrictions based on a ‘need-to-know’. They will assign an endorsement marking or compartmented marking to indicate the ‘need-to-know’ compartment which will identify the special handling requirements for the information.
Requesting access to ‘need-to-know’ compartmented information
In most normal circumstances, ‘need-to-know’ is a two-way process that relies both on the agency holding the information and on the requestor making a reasonable request, i.e., an individual or agency should only request information when it needs it to carry out its functions. It is not sufficient to request information just because you want to know – there must be a legitimate need for the request. Further, the ‘gatekeepers’ of information requests may lack the knowledge to know if an information request by another person or agency is reasonable or not.
Agencies holding information still maintain a responsibility to check whether information should be shared. However, effective information sharing will be better enabled if agencies assume information sharing requests are made in good faith and supported by professional judgement.
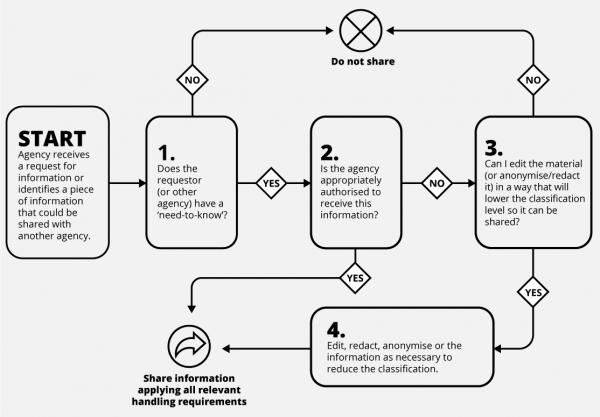
Need to know principle flow chart
The need-to-know process is a two or three step process that can be applied to any information sharing.
- Step 1 confirms whether a ‘need-to-know’ exists. If there is not a valid reason to access information, it should not be provided. Step 1 confirms whether somebody should receive information.
- Step 2 confirms whether the person receiving the information is appropriately authorised to hold it. This might mean that they have the appropriate security clearance and/or systems and locations accredited to manage classified information. In a commercial setting, it might mean confirming a contractor has signed a non-disclosure agreement before sharing business information.
- If the decision at Step 2 is ‘no’, step 3 asks whether information can be provided in a different format (e.g. by removing some more sensitive pieces of information).
